Credentials presentation flow
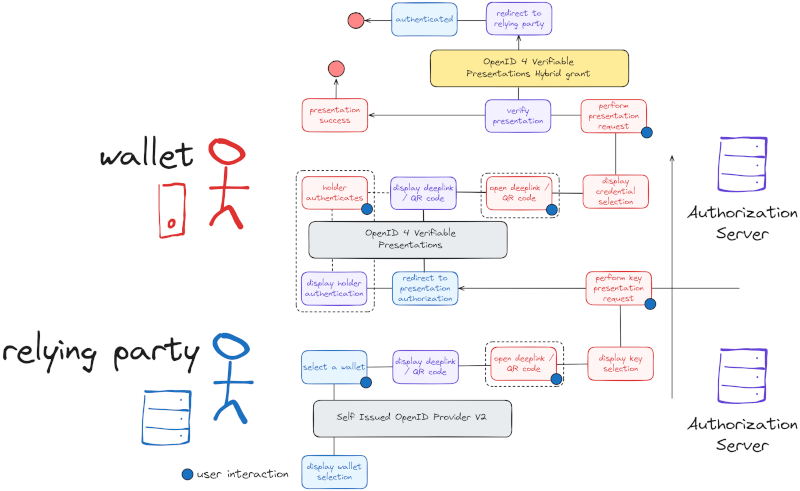
2-step presentation
In order to securely present credentials, on top of OID4VP the server suggest as an option to force the verification of the presentations vp_token against the given client_id. This way, you can use SIOPV2 to fetch the required OpenID 4 Verifiable Presentations client_id and provide a DID given by the id_token from the first step. Then, That client_id will be later used to verify the presentation vp_token signature in the last step.
This 2-step flow prevents from QR code / deeplink stealth, reducing to one target the attack surface of such stealth. The authorization link of OpenID 4 Verfiable Presentations being attached to the public key provided by SIOPV2 and being already cryptographically verified by the flow, the attacker can forward a QR code / deeplink only valid for a single victim. The integrated wallet mitigates this by creating a session to store the SIOPV2 given key to ensure the client_id match that key.