(WIP) boruta identity platform documentation
What is boruta?
boruta is an OAuth 2.0 and satellites specifications authorization server implementation. As an Identity and Access Management solution, it helps centralize authorization and identity related issues within your infrastructures. boruta stands as a server that help for the users to authenticate and to expose and apply access rules for your HTTP services (APIs) enabling better security. On top of current identity infrastructures, boruta implements decentralized identity specifications enabling it to provide a secure issuer and verifier along with an integrated wallet.
boruta is composed of an authorization server, an administration interface, an identity provider and an experimental gateway for gathering all API security related needs for a serivce composed of one or more backends. It enables to have Single Sign On and identity federation capabilities following the OAuth 2.0 framework.
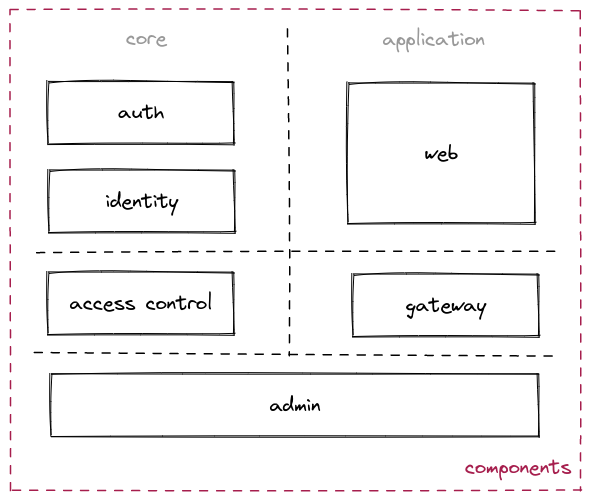
Open core / Application layer architecture
boruta is splited into an open core and an application layer giving from one side the authorization business logic and the other the exposition and authentication topics to provide a standalone server. This core is open source and avalilable as an Elixir package on hex.pm.
Why another authorization server?
boruta has been designed to be both end-user and developer friendly. With a high level of customization, it helps to have an immersive experience for your users giving them custom interfaces. The administration interface gives an exhaustive set of configuration switches that is also accessible through REST API calls for automation.
As an open-source product, it takes the advantage to being backed by a community of developers making it a secure and extensible solution. All suggestions, feature requests, or any kind of contribution will be very welcome.
Have a look at the GitHub repository
With an implementation of OpenID 4 Verifiable Credentials Issuance (OID4VCI) and OpenID 4 Verifiable presentations (OID4VP), boruta provides means to be compliant with the eIDAS 2.0 regulation. On top of those protocols, it brings ways to get identities from a data source still being secure and with low integration costs, being part of your infrastructure by addition, not replacement. Indeed, boruta can leverage identity federation to restrict access to verifiable credentials making it a secure and privacy preserving solution.
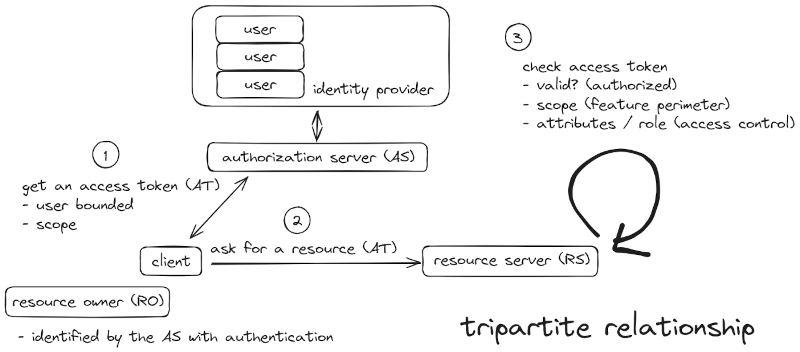
About an identity provider
boruta comes up with an integrated idenity provider, it can both store the users' credentials internaly and connect to a LDAP compliant server (Active Directory is). It helps more than enable password authentication abilities, to enhance users with features like having custom attributes, enforce email confirmation, or consent to the client's requested scopes.
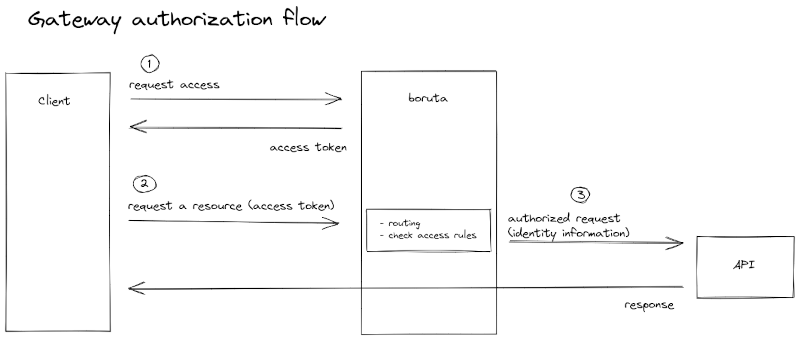
About a gateway
boruta is coupled to a Work In Progress gateway that acts as a reverse-proxy sitting between your frontends and backends in order to apply security rules in a fast and non-intrusive way. To perform those access restrictions, the gateway is based on boruta-provided access tokens and according granted scopes to mitigate the traffic and allows to get access to OpenID profile attributes in a secure way.
Implemented specifications and certification
As it, boruta server aim to follow the RFCs from IETF:
- RFC 6749 - The OAuth 2.0 Authorization Framework
- RFC 7662 - OAuth 2.0 Token Introspection
- RFC 7009 - OAuth 2.0 Token Revocation
- RFC 7636 - Proof Key for Code Exchange by OAuth Public Clients
- RFC 7521 - Assertion Framework for OAuth 2.0 Client Authentication and Authorization Grants
- RFC 7523 - JSON Web Token (JWT) Profile for OAuth 2.0 Client Authentication and Authorization Grants
- RFC 9449 - OAuth 2.0 Demonstrating Proof-of-Possession at the Application Layer (DPoP)
- RFC 9126 - OAuth 2.0 Pushed Authorization Requests
And the specifications from the OpenID Foundation:
- OpenID Connect core 1.0
- OpenID Connect Dynamic Client Registration 1.0 incorporating errata set 1
- OpenID for Verifiable Credential Issuance
- Self-Issued OpenID Provider v2
- OpenID for Verifiable Presentations - draft 21
This server has been certified for the Basic, Implicit, and Hybrid OpenID Provider profiles by the OpenID Foundation on October, 18th 2022 for the tagged versions 0.1.0 and 0.5.0
This server has been certified for the Config and Dynamic OpenID Provider profiles by the OpenID Foundation on May, 16th 2023 for the tagged version 0.2.0

This server has also been certified against the European Blockchain Service Infrastructure (EBSI) issuance test suite for the tagged version 0.4.0 and for verifiable credential verification for the tagged version 0.5.0.


Navigation
- Getting up and running - Quickstart
- Understand how to configure the server - provider configuration