Clients configuration | Authentication
Client attributes help to manage the authorization capabilities for OAuth 2.0 and satellites flows. They provide a high level of customization helping the server to be integrated within infrastructures seamlessly. Those configuration help the flows to be both business and technically adapted for the addressed use case.
OAuth clients can be customized through either the Administration API or the user interface providing 4 categories of settings:
- General configuration
- Authentication
- Security
- Grant types
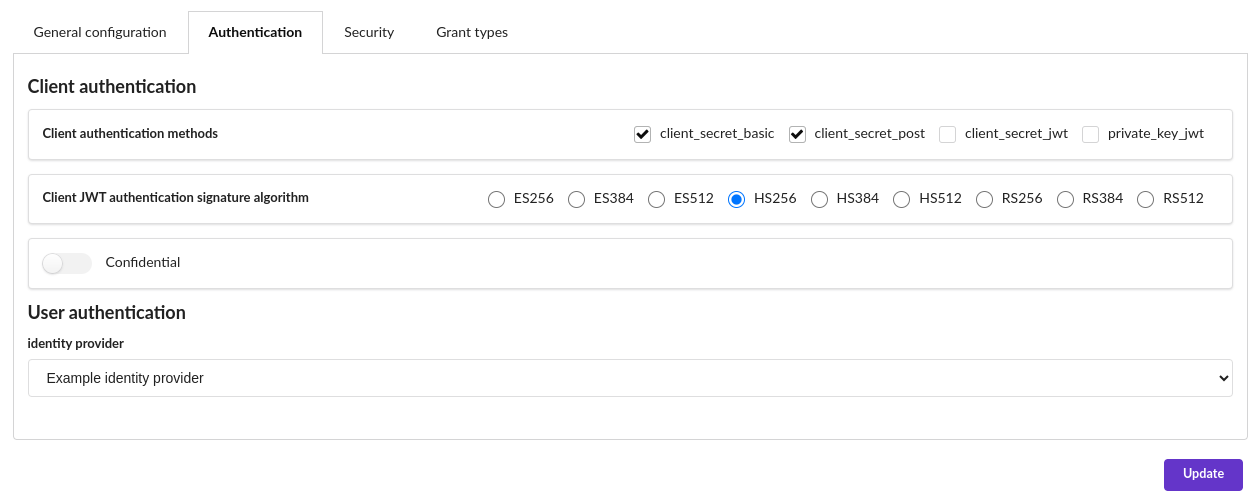
Authentication parameters
OAuth Client authentication
Client authentication methods enables to select the client supported authentication methods:
- client_secret_basic uses HTTP basic to authenticate the client provided the
client_idand theclient_secret - client_secret_post uses HTTP POST method to authenticate the client provided the
client_idand theclient_secret - client_secret_jwt parses the request JWT that is to be signed using a symetric algorithm given the
client_secret - client_private_key parses the request JWT that is to be signed using an asymetric algorithm given the provided public key
Client JWT authentication signature algorithm gives ways to select the used client JWT signature algorithm. Have to be symetric for client_secret_jwt and asymetric for client_private_key.
Confidential define if the client is set to be confidential as stated in OAuth 2.0 specification.
The access to most of the OAuth and OpenID Connect provider endpoints is protected by providing a couple client_id / client_secret aiming to identify the client that performs the request. As stated in OAuth 2.0, the server gives the ability to set clients as confidential requesting the client secret in more cases. Rules of requesting client credentials acts as follow:
- Client Credentials - always enforces check of the client's secret
- Authorization Code Grant - enforces check of client secret only for confidential clients on access token request, does not check client secret during the authorization phase
- Hybrid Flow - has the same behavior as the authorization code grant
- Implicit Grant - does not check the client's secret
- Resource Owner Password Credentials - enforces check of client secret only for confidential clients
- Refresh Token - always enforces check of client secret,
public_refresh_tokenoverrides the confidentiality - Introspect - always enforces check of the client's secret
- Revoke - always enforces check of client secret,
public_revokeoverrides the confidentiality
User authentication
identity provider enables to select the means of authentication for the users provided by an Identity Provider
User interface