Identity providers configuration
Identity providers are the server resources helping to customize the end-user authentication interface. Those means of authentication provide customizable flows and interfaces that help to keep the service branding while providing authentication for them in a seamless way. In case of misconfiguration in navigation error from the end-user, fallbacks to error templates are provided to keep a good end-user experience.
Architecture
For each client, you can configure a specific identity provider, that will be associated to a backend, helping to provide both authorization and authentication for them. This way, each client will have a custom interface as mean of authentication for the end-users.
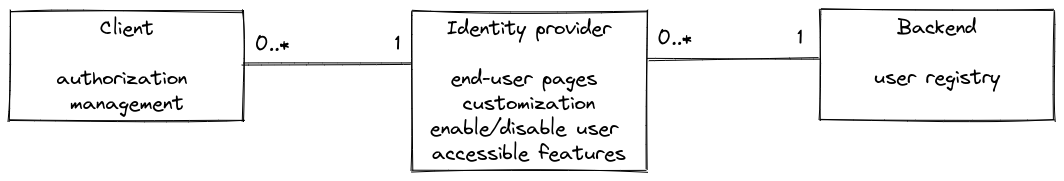
Have a look at client configuration
Have a look at backend configuration
Manage through User Interface
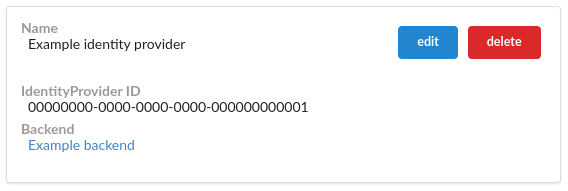
The administration interface gives the ability to create, update and delete identity providers. You can access them by navigating to the Identity providers > identity provider list section in the sidebar menu.
Manage through API
All identity provider operations are accessible through a REST API following the below description. All identity provider management endpoints are protected with a Bearer token that can be obtained with any OAuth flow. In order to get access, you need to have an access token with the private scope identity-providers:manage:all granted.
Have a look at API documentation